- CER found 13.3% of wallets underwent penetration testing, often on older versions.
- Popular brands like MetaMask, ZenGo, and Trust Wallet showed security measures through testing.
- MyAlgo and Atomic Wallet incidents highlight urgent need for robust wallet security in 2023.
In a report released in July by CER, a platform specializing in cybersecurity certification, it was revealed that out of 45 different brands of cryptocurrency wallets, merely six, equivalent to 13.3% of the total, have engaged in penetration testing aimed at uncovering potential security weaknesses. Additionally, among these, only half have conducted such tests on their most up-to-date product versions.
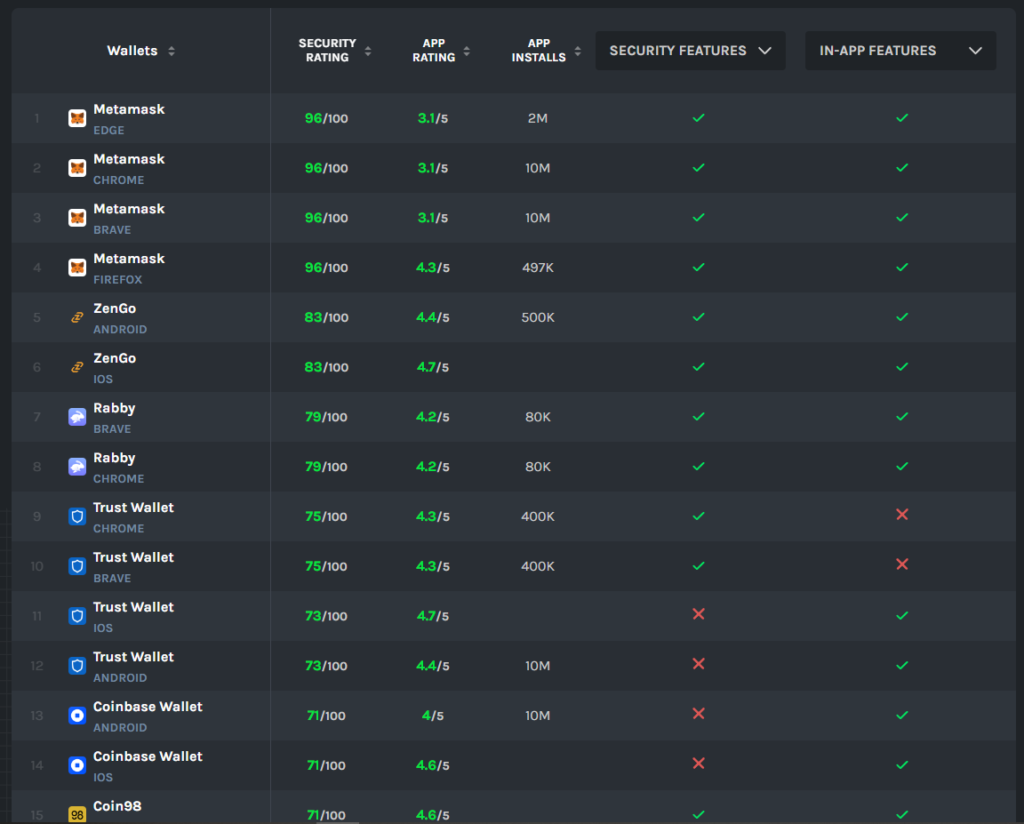
As per the report, MetaMask, ZenGo, and Trust Wallet emerged as the three brands that conducted recent penetration tests. The assessment indicated that Rabby and Bifrost carried out penetration testing on earlier software editions, while LedgerLive’s testing version was unspecified (“N/A” in the report). Notably, the remaining brands on the list failed to present any substantiation of undergoing such assessments.
Furthermore, the report included a comprehensive security ranking for each wallet. MetaMask, ZenGo, Rabby, Trust Wallet, and Coinbase Wallet were highlighted as the most secure wallets in the overall evaluation.
What Is Crypto Wallet Penetration Testing?
Penetration testing, often referred to as “pen testing,” is a systematic approach employed to uncover security vulnerabilities within computer systems or software. In this practice, a security researcher takes on the role of an attacker, attempting to breach the device or software in ways that were not originally intended. Typically, the penetration tester operates with minimal or no prior knowledge of the product’s inner workings. This method replicates real-world hacking scenarios, aiding in the identification of potential weaknesses prior to the product’s official release.
According to CER’s findings, a significant majority of 39 out of the 45 wallet brands refrained from conducting any form of penetration testing, even on previous iterations of their software. CER suggested that this trend could possibly be linked to the costs associated with these tests, particularly for companies that frequently release updates to their products. They stated, “This can be attributed to the frequency of updates that an average application undergoes, where each new update has the potential to render the previous penetration test ineffective.” The research also revealed that wallet brands with higher popularity were more inclined to engage in security audits, including penetration testing, due to their comparatively more substantial financial resources.
“Essentially, popular wallets tend to adopt more robust security measures to protect their increasing user base. This seems logical – a higher user base often corresponds to more significant funds to secure, more visibility, and consequently, more potential threats. It can also result in a positive feedback loop, with more secure wallets attracting new users in higher numbers than the less secure ones.”
CER
CER’s assessment of wallets was established through a methodology encompassing factors such as bug bounties, historical incidents, and security attributes like recovery methods and password prerequisites.
Even though the majority of wallet brands refrain from conducting penetration testing, CER noted that many of them rely on bug bounties as a proactive approach to discovering vulnerabilities, often proving effective in thwarting hacking attempts. Among a total of 159 individual wallets evaluated, 47 received a “secure” rating, signifying a security score exceeding 60. Notably, this pool included wallets from the same brands, for instance, MetaMask for Edge browser and MetaMask for Android were treated as distinct entities.
In the year 2023, wallet security has assumed heightened importance due to the web wallet MyAlgo, which experienced a security breach in late February, leading to an estimated user loss of over $9 million.
I haven’t seen many posts about this on CT yet but it’s suspected over $9.2m (19.5M ALGO, 3.5m USDC, etc) has been stolen on Algorand as a result of this attack from Feb 19th to 21st.
— ZachXBT (@zachxbt) February 28, 2023
ChangeNow shared they were able to freeze $1.5m. https://t.co/BPCXTUD57n pic.twitter.com/A3t7Ss0e83
Another incident affected the Atomic Wallet hack on June 3, which resulted in losses surpassing $100 million. The Atomic team speculated that the breach might have resulted from a virus or malware injection into the company’s infrastructure, although the precise vulnerability exploited remains unidentified.